Grow your
social channels
to the next level
Kickstart your Instagram, Youtube, Spotify &
other channels presence, credibility & interactions
with the incredible service of the Top Rated
Social Media Marketing Company
Grow your
social channels
to the next level
Kickstart your Instagram, Youtube, Spotify
& other channels presence, credibility &
interactions with the incredible service
of the Top Rated Social Media
Marketing Company
Top 3 reasons to choose BuildMyPlays
 | High Quality & Fast Delivery Customers surely receive 100% high-quality services and delivered within 24 hours. |
 | Retention Guarantee Money-back and Retention guarantee are applied on all packages. |
| Customer Support 24/7 It doesn’t matter if it’s 3AM or middle of the day, we are always here to help. |
Top 3 reasons to choose BuildMyPlays
 | High Quality & Fast Delivery Customers surely receive 100% high-quality services and delivered within 24 hours. |
 | Retention Guarantee Money-back and Retention guarantee are applied on all packages. |
| Customer Support 24/7 It doesn’t matter if it’s 3AM or middle of the day, we are always here to help. |
Our Services
| Gain high quality & targeted followers, likes & comments. Be viral can’t be easier. |
Instagram Followers >>
Starting from $0.036/Follower
Automatic Instagram Likes/Views >>
Starting from $0.022/Like, $0.004/View
Instagram Likes, Views & Comments >>
Starting from $0.075/Like, $0.009/View, $1/Comment
 | Get safe, HR YouTube views on all of your videos instantly. Success is just a few clicks away. |
HR YouTube Views >>
Starting from $0.017/View
YouTube Subscribers >>
Starting from $0.18/Subcriber
YouTube Likes and Comments >>
Starting from $0.12/Like, $0.5/Dislike, $2/Comment
 | Gain more followers and views easily with 100% satisfaction guaranteed services. |
TikTok Followers >>
Starting from $0.036/Follower
TikTok Views >>
Starting from $0.0018/View
TikTok Likes >>
Starting from $0.03/Like
 | The quickest way to gain more followers and plays. Enhance your music career on Spotify. |
Spotify Plays >>
Starting from $0.012/Play
Spotify Followers >>
Starting from $0.03/Follower
Spotify Monthly Listeners >>
Starting from $0.01/Listener
 | Attract more listeners, followers & engagements easily. Just focus on making awesome music. |
SoundCloud Plays >>
Starting from $0.0024/Play
SoundCloud Followers >>
Starting from $0.12/Follower
SoundCloud Likes, Reposts & Comments >>
Starting from $0.09/Like, $0.12/Repost, $0.8/Comment
| Gain more Threads followers and likes can not be easier. Get ahead of the game! |
Instagram Threads Followers>>
Starting from $0.04/Follower
Instagram Threads Automatic Likes>>
Starting from $0.04/Like
Instagram Threads Likes>>
Starting from $0.045/Like
 | Easy way to boost your page likes, post likes, comments and everything else… |
Facebook Page Likes >>
Starting from $0.072/Like
Facebook Profile Followers >>
Starting from $0.036/Follower
Facebook Post Likes, Shares & Comments >>
Starting from $0.08/Like, $1/Comment
 | Gain more followers, receive automatic retweets & favorites, get recommended by popular influencers. |
Twitter Followers >>
Starting from $0.06/Follower
Twitter Retweets and Favorites >>
Starting from $0.18/Like, $0.18/Retweet
Automatic Twitter Likes/Retweets >>
Starting from $0.04/Like, $0.06/Retweet
| Buy awesome Mixcloud followers, plays, likes & repost. 100% satisfaction guaranteed. |
MixCloud Plays >>
Starting from $0.0012/Play
MixCloud Followers >>
Starting from $0.1/Follower
MixCloud Likes & Reposts >>
Starting from $0.09/Like, $0.09/Repost
Our Services
| Gain high quality & targeted followers, likes & comments. Be viral can’t be easier. |
Instagram Followers >>
Starting from $0.036/Follower
Automatic Instagram Likes/Views >>
Starting from $0.022/Like, $0.004/View
Instagram Likes, Views & Comments>>
Starting from $0.075/Like, $0.009/View, $1/Comment

 | Get safe, HR YouTube views on all of your videos instantly. Success is just a few clicks away. |
HR YouTube Views >>
Starting from $0.017/View
YouTube Subscribers >>
Starting from $0.18/Subcriber
YouTube Likes and Comments >>
Starting from $0.12/Like, $0.5/Dislike, $2/Comment
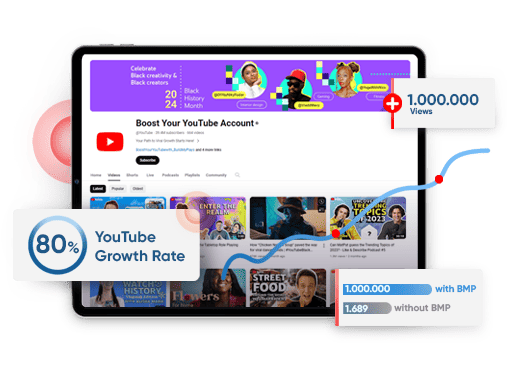
 | Gain more followers and views easily with 100% satisfaction guaranteed services. |
TikTok Followers >>
Starting from $0.036/Follower
TikTok Views >>
Starting from $0.0018/View
TikTok Likes >>
Starting from $0.03/Like
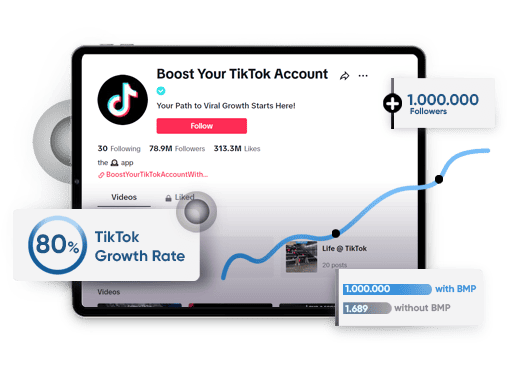
 | The quickest way to gain more followers and plays. Enhance your music career on Spotify. |
Spotify Plays >>
Starting from $0.012/Play
Spotify Followers >>
Starting from $0.03/Follower
Spotify Monthly Listeners >>
Starting from $0.01/Listener
 | Attract more listeners, followers & engagements easily. Just focus on making awesome music. |
SoundCloud Plays >>
Starting from $0.0024/Play
SoundCloud Followers >>
Starting from $0.12/Follower
SoundCloud Likes, Reposts & Comments >>
Starting from $0.09/Like, $0.12/Repost, $0.8/Comment
| Gain more Threads followers and likes can not be easier. Get ahead of the game! |
Instagram Threads Followers>>
Starting from $0.04/Follower
Instagram Threads Automatic Likes>>
Starting from $0.04/Like
Instagram Threads Likes>>
Starting from $0.045/Like
 | Easy way to boost your page likes, post likes, comments and everything else… |
Facebook Page Likes >>
Starting from $0.072/Like
Facebook Profile Followers >>
Starting from $0.036/Follower
Facebook Post Likes, Shares & Comments >>
Starting from $0.08/Like, $1/Comment

 | Gain more followers, receive automatic retweets & favorites, get recommended by popular influencers. |
Twitter Followers >>
Starting from $0.06/Follower
Twitter Retweets and Favorites >>
Starting from $0.18/Like, $0.18/Retweet
Automatic Twitter Likes/Retweets >>
Starting from $0.04/Like, $0.06/Retweet
| Buy awesome Mixcloud followers, plays, likes & repost. 100% satisfaction guaranteed. |
MixCloud Plays >>
Starting from $0.0012/Play
MixCloud Followers >>
Starting from $0.1/Follower
MixCloud Likes & Reposts >>
Starting from $0.09/Like, $0.09/Repost
Customers
100,000+
Projects Promoted
140,000+
Followers delivered
14,377,688
Views/Plays delivered
75,614,430
Customers
100,000+
Projects Promoted
140,000+
Followers delivered
14,377,688
Views delivered
75,614,430
Customer Feedback & Reviews
Here at BMP we pride ourselves in exceptional service and affordable prices.
Don’t just take our word for it – check out what customers say about our products below.
Customer Feedback & Reviews
Here at BMP we pride ourselves in exceptional service and affordable prices.
Don’t just take our word for it – check out what customers say about our products below.
How it works
Step 1
Place Order
Step 2
Receive Confirmation Email
Step 3
Start promoting with partner
Step 4
Enjoy the result with 90 Days Guarantee
How it works
Step 1
Place order
Step 2
Receive Confirmation Email
.
Step 3
Start promoting with partners
Step 4
Enjoy the result
Your Social Media Success Starts Right Here
Would you like to read?
We share a range of different topics quite often. Make sure to check out our blog if you want to stay in touch with the latest news … and beyond!